As an industry-leading ERP service provider, we staunchly believe that a watertight security system is the cornerstone of every successfully running custom CRM software. At Arobit Business Solutions Pvt Ltd, we ingrain security into every step of the software development life cycle (SDLC). We pay minute attention to multiple elements of security right through the inception phase rather than leaving scope for stumbling upon errors and defects post-product delivery.
This helps our clients save a considerable deal of money and time while also keeping security vulnerabilities at bay.
Factors We Consider When Providing Supremely Secure CRM Development Services
As a pioneer CRM software development company, we follow a range of security measures from the earliest stages of software development as discussed below -
1. Error Reporting
Error reporting helps with the identification, tracking, and resolution of errors in software, mobile applications, or web services to facilitate the seamless development and deployment of the desired digital product. It also aids in finding the root cause of the issue, allowing developers to kill the concern at the core. For example, it helps in finding spelling mistakes in our variables and detecting faulty function usage, among other things.
However, once our system goes live, we archive all the error reports as it can give users a chunk of critical details about our functioning, such as the software we run, our folder structure, etc. Therefore, we log our errors to a protected file with the PHP function set_error_handler.
2. Register Globals (register_globals)
Register Globals or register_globals was meant to help rapid application development. You may consider the following URL for instance, http://oursystem.tld/index.php?var=1, which includes a query string. The register_globals statement lets us automatically access the value with $var instead of $_GET['var']. Although it may sound useful at first glance, unfortunately, all variables in the code now have this property.
Additionally, we can now easily get into PHP applications that do not protect against this unintended consequence.
Here's a code snippet that we commonly see in PHP scripts:
If( !empty( $_POST[‘username'] ) && $_POST['username'] == 'test' && !empty( $_POST[' password'] )
&& $_POST['password'] == "test123" )
{
$access = true;
}
If the application runs with register_globals enabled, the user may place access=1 into a query
string, and access whatever the script is running.
3. Magic Quotes (magic_quotes_gpc, magic_quotes_runtime, magic_quotes_sybase)

Originally, magic quotes were a feature of the PHP scripting language in order to assist newcomers in writing functioning SQL commands without requiring manual escaping. It prevents developers from writing code that is prone to the threats of SQL injection. It also shielded the programmers from the hassle of using addslashes() and other similar security features in their code.
However, it is also essential to understand the challenges associated with magic quotes.
If both magic quotes and addslashes () are used, we end up with multiple slashes being added, causing errors.
If we assume that the magic quotes are turned on and it isn't so, all the input goes unchecked.
Magic quotes escape only single and double quotes. On the other hand, if we use a database engine, many database-specific characters also need to be escaped. It is, therefore, highly advisable to disable this feature and use proper variable validation instead.
4. Validate Input
One of the most effective ways of safeguarding the system against security threats is by ensuring our users can only enter the appropriate data. If the entered data in the form is not validated as right, then it would immediately indicate an error rather than sending it to the database for login or other credential validation. The input field in every form shall have a layer of validation before it’s sent to the database.
5. Handling Cross System Scripting (XSS) Attacks in User Input
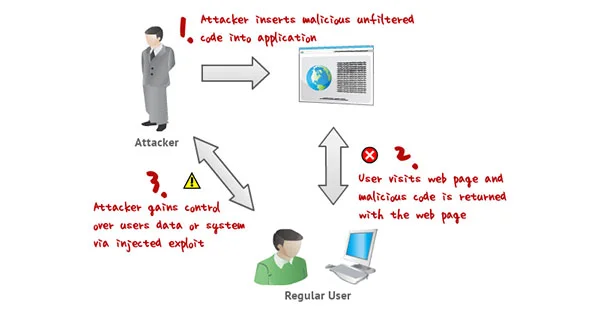
Typically, a web application accepts input from users and displays it in a variety of forms, such as comments, threads, or blog posts that are in the form of HTML code. However, it would be dangerous to allow HTML while accepting an input since that allows for the execution of JavaScript in unanticipated ways. A single flaw may also lead to the hijacking of cookies, and the compromised cookie data could be abused to fake a real account and give an illegal user access to the web system's data.
If we require the HTML to be mostly disabled while still allowing simple formatting, we can allow just a few selected HTML tags (without attributes) such as or . Alternatively, we can allow a
popular set of tags called "BBCode" or "BB Tags". It is an effective way to allow some formatting customization while simply blocking the threats. We can execute BBCode using pre-existing packages such as HTML_BBCodeParser or write our BBCode implementation with regular expressions and a series of preg_replace statements.
6. Protecting Against SQL Injection
SQL injection attacks happen when data is entered without being verified, and the application fails to escape characters used in SQL strings such as single quotes (') or double quotes (").
If these characters are not filtered, the users can exploit the system by making queries always true and thus letting them trick login systems.
MySQLi allows us to do this either with the mysqli_real_escape_string function when connected to a server or with prepared statements.
Prepared statements are a way of distinguishing SQL logic from the data that is being passed to it. The
functions used within the MySQLi library filter the input for us, which can be understood as follows-
$id = $_GET['id'];
$statement = $connection->prepare( "SELECT * 3. FROM tbl_members WHERE id = ?" );
$statement->bind_param( "i", $id );
$statement->execute();
It is essential to note about the "i" in bind_param Is that i stands for integer, and we can use s for string, d for double, and b for blob based on the kind of data we are passing.
Although this will protect us in most circumstances, we must still lay strong emphasis on proper data validation as mentioned previously.
Secure Your Success With Our Robust Mechanisms For Software Security
With our highly proficient team of developers, testers, and other IT experts, we've successfully helped several businesses, regardless of their size and scale, seamlessly achieve their innovation and technological objectives. Get in touch with the top-grade ERP software development company, and get the best-in-class and super secure software solutions, now!