Data security has taken the front seat in the Software Development Lifecycle (SDLC) given the massive volumes of data that continuously flow between different endpoints throughout the process. While malicious actors are on the constant lookout for new ways to find and exploit the vulnerabilities of software systems, we at Arobit Business Solutions Pvt Ltd leave no stone unturned in staying ahead of it all.
As one of the leading ERP service providers in India, we prioritize security across the development lifecycle, and it helps our expert developers and stakeholders grasp more time and scope to troubleshoot threats, and address all the key security aspects well in advance.
How Does Team Arobit Address Key Security Aspects In CRM Development Services?
We at Arobit hold security at the core of our software development process. Here's how we go about addressing the key security aspects -
1. Strong Passwords

To ensure the maximum strength of passwords and ensure an effective authentication of the user's access to the enterprise systems, our developers add controls for maintaining the minimum length and complexity requirements for all passwords. The passwords are accepted and confirmed only if they match the requisite criteria. Plus, the password strength checker and accepter algorithm is self-made. Simultaneously, we also ensure that the password does not become excruciatingly complex.
2. Error Reporting
No matter how efficient the software is, there's always some room for unintended errors pertaining to code, different updations, integrations, and interactions. To catch hold of the issues early on, we employ an exhaustive error reporting process that helps us clearly identify, track, and work towards resolving the potential concerns in software, mobile applications, as well as web services.
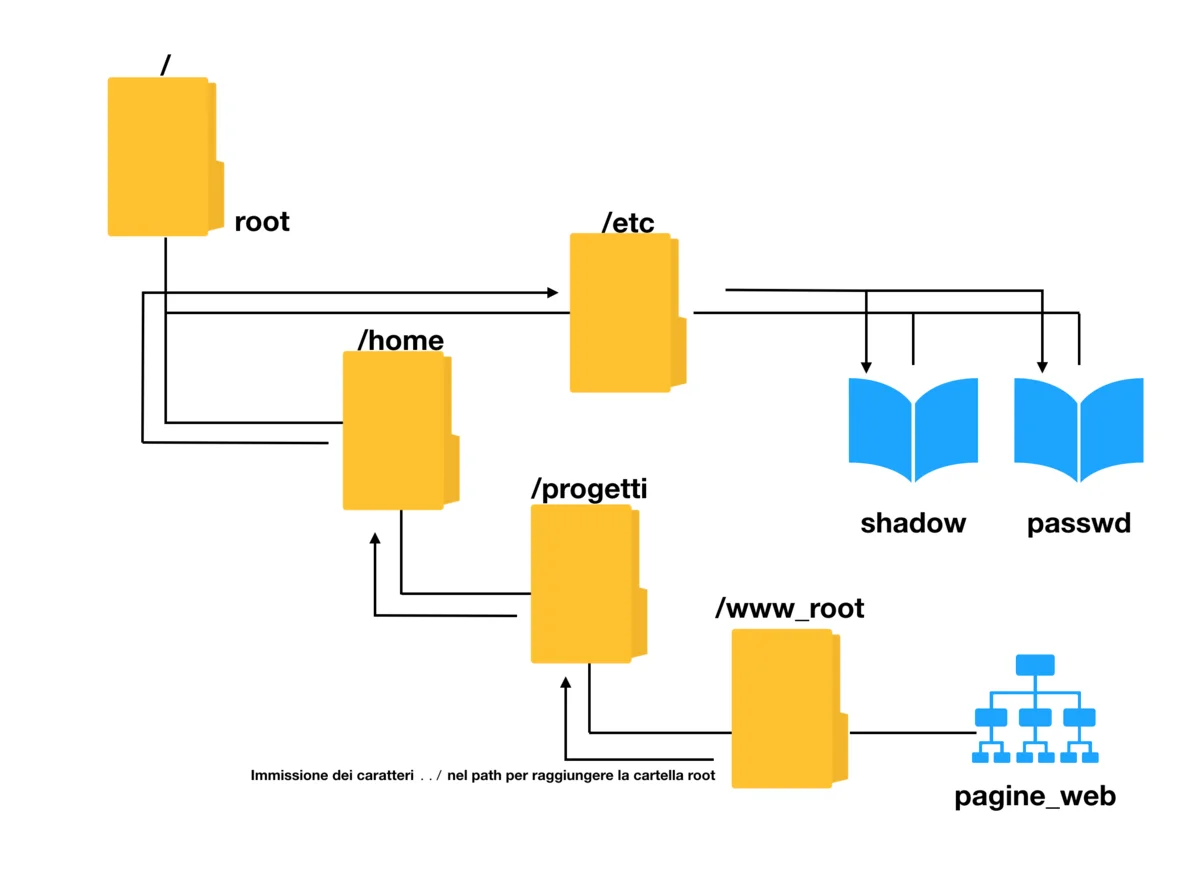
3. Preventing Directory Traversal
Directory traversal or file path traversal is a web security threat that lets the attacker read and modify arbitrary files on the web server that is running an application. These files may comprise the application code, important credentials for back-end systems, and other crucial data relating to the operating system. We fully prevent such intrusions by using effective techniques, such as indirection, sanitizing filename parameters, running the server with restricted permissions, and much more.
4. Taking Care Of Cross System Scripting (XSS)
Cross-site scripting (XSS) is a cybersecurity attack in which the attacker injects a malicious script into content from genuine websites. These malicious scripts are often delivered in the form of bits of JavaScript code, Ajax, and Hypertext Markup Language (HTML), among others. Our team works to prevent such XSS attacks by testing the XSS vulnerabilities, finding, analyzing, sanitizing, and validating the inputs.
5. Using SSL For Secure Communication

We use secure socket layer (SSL) protocol to secure communication between the host and the web server with the help of public key infrastructure (PKI) technology. The SSL certificate enables SSL communication, authenticates the identity of the server, and allows for smooth and encrypted transmission of the data.
It will help you assert your business's digital identity and legitimacy and secure your users’ data against man-in-the-middle (MitM) attacks, eavesdropping, data leaks, ISP snooping, and other privacy vulnerabilities. Additionally, it also increases your chances of better Google rankings.
6. Maintaining The Code Integrity
To ensure a flawlessly secure system, we maintain all code in safe repositories letting only authorized users access the data. We keep a close eye on all the activities, and code signing process, while also constantly monitoring the changes.
7. Regularly Reviewing And Testing The Code
Rather than testing the code toward the end of the SDLC, we leverage developer reviews and automated testing to efficiently evaluate the code for any gaps. Our regular review of the code helps in saving money and time on both developer's and client's end. As a top CRM software development company, team Arobit is always proactive with well-thought strategies and processes to address the existing and potential cyber threats in real-time.
Grasp The Benefits Of Secure Custom CRM Software With Arobit
Choosing Arobit Business Solutions Pvt Ltd as your security-driven software development partner, ERP software development company, or CRM development service expert will throw open a bunch of benefits your way. You can experience the improved performance of your software, minimal Scope of cyber threats, lesser cost of issue diagnosis and fixation, thorough compliance with security standards, and greater levels of customer trust and loyalty. Contact us today!